Preface
A pfBlocker guide has frequently been requested as an addition to my baseline configuration guide. I’ve been working on a guide for some time now but with the constant evolution of pfBlocker and pfSense its never quite been ready for release. I’ve decided to break the guide into two sections to allow me to get some information published. The first part will focus on the more stable IP blocking functionality of pfBlocker. A second part to be published later, will focus on pfBlockers DNS blocking capabilities that are still undergoing more significant development.
Please feel free to email with feedback. I’m interested in hearing about other use cases you have found for pfBlocker too.
pfSense pfBlockerNG configuration guide
Last revised 20 April 2020.
Contents
- Introduction
- What is pfBlockerNG?
- How do I use pfBlocker?
- How does pfBlocker work?
- Installation
- pfBlockerNG Foundation Configuration
- Malicious IP Address Blocking
- Policy based routing with a custom IPv4 list
- Restrict WAN port access by GeoIP whitelist
- Submitting new lists for inclusion in Feeds page
- References
- Change Log
Introduction
This guide aims to demonstrate how to use pfBlockerNG to manage ingress and egress from a SOHO network through the use of blocklists, it’s built as an extension of my pfSense baseline setup guide detailed here.
What is pfBlockerNG?
pfBlockerNG is a pfSense package created by BBCan177 based upon the previous work of Marcello Coutinho and Tom Schaefer. The intent was to extend pfSense’s core firewall functionality with the ability to further control and manage inbound and outbound access through the firewall with the use of IP and DNS control lists. You can support BBCan177 and the ongoing development work directly though his Patreon page here.
IP Blocking
pfBlockerNG provides the ability to curate firewall rules based on both IPv4 and IPv6 address spaces. These rules can be used to control both ingress and egress traffic on single or multiple interfaces.
DNS Blocking
pfBlockerNG also has the ability to control access to the DNS Resolver to prevent access to malicious sites. Domain blocking can be used for advert, tracking and malicious domain filtering.
How do I use pfBlocker?
pfBlocker is highly versatile and powerful tool and there are many ways to implement it. My preference is to use pfBlocker to manage aliases and then use those aliases in manually crafted firewall rules ensuring both scope and ordering is correct for my intended purpose. I find this offers a level of precision not available when using the automatically generated rules.
Inbound traffic filtering
pfSense by default blocks all inbound traffic so unless there are open ports on your firewall, there is zero additional protection offered in applying any rules to inbound traffic. I have a number of ports open exposing a VPN end point and several self-hosted services so make use of both custom IP lists and GeoIP restrictions to limit access.
Outbound traffic filtering
I use outbound blocking on my primary use subnets (VL20_VPN & VL30_VPN) to prevent users from inadvertently accessing malicious sites. Coupled with logging this is a useful way to spot possible compromised devices.
Policy based routing
I use several custom aliases that are used in policy based routing firewall rules to direct traffic out of specific gateways or gateway groups.
Malicious DNS Blocking and advert limiting
I apply DNS blocking to the subnets served by the DNS Resolver to prevent access to tracking and/or malicious locations. I apply pretty limited filtering to avoid the potential of introducing false positives.
How does pfBlocker work?
Before we get to installation and configuration, its worth understanding how pfBlocker takes raw blocklists and turns them into a final blocklist which is loaded into the firewall and/or DNS Resolver. Its actually a fairly complex process so this is a simplified representation.
- As per pfBlockerNG's CRON schedule, the following processes will run (assuming they have been enabled).
- DNS blocklists processed
- Geo location data processed, GeoIP lists updated
- IPv4/6 lists processed, each list in turn checked against their update frequency and if neccessary, updated.
- list processed by de-duplication (IPv4 only)
- list processed by suppression (IPv4 only)
- list processed by CIDR aggregation
- list processed by Reputation Max
- Aggregated Group list processed by Reputation pMax and dMax
- DNS Resolver reconfigured
- Firewall reconfigured
Those key stages are described in some more detail below.
DNS Blocklist Processing
Optimised DNS Resolver blocklists are generated from domain names gathered from various blacklist sources or manually entered.
GeoIP processing
Geolocation is the identification or estimation of the real-world geographic location of an IP address. pfBlockerNG makes use of lists provided and maintained by MaxMind.
De-duplication
Attempts to reduce list size by detecting and removing duplicate entries.
Suppression
Removes any deny list entries that match those specified in the Suppression list which can be populated manually or from the pfBlockerNG alerts tab. RFC1918 and loopback addresses are also filtered when enabled.
CIDR aggregation
Attempts to reduce overall list size by two methods.
Removing superfluous prefixes because they are already included in another prefix, for example, 203.97.2.0/24 would be removed if 203.97.0.0/17 was also present.
Combining adjacent prefixes under a single, shorter-length prefix. For example, 203.97.2.0/24 and 203.97.3.0/24 can be combined into the single prefix 203.97.2.0/23.
CIDR aggregation is processor intensive, if you are running on a low powered device you may need to disable this feature.
Reputation
A set of more aggressive aggregation techniques which if used carelessly could introduce additional false positives to your lists. For example, if processing a subnet with pMax[50] that has 50 positive matches, the whole subnet will be blacklisted possibly including some addresses which were not included in the original blocklist.
Reputation Max will search for repeat offenders in an individual blocklist. Once the Max setting is reached, the whole subnet will be blocked.
Reputation pMax will search for repeat offenders in all blocklists, without using country Code Exclusion. Once the pMax setting is reached, the whole subnet will be blocked.
Reputation dMax will search for repeat offenders in all blocklists using country code exclusion. Once the dMax setting is reached, the whole subnet will be blocked.
Sample Processing Results
To provide some perspective into the efficiency of these methods, I’ve shared some of my test results on the ‘PRI1’ list below. Hopefully this is useful helping to establish the right balance between performance and accuracy.
| total # | reduction # | reduction % | |
|---|---|---|---|
| PRI1 (16-Mar-2020) | 32544 | - | - |
| Dedupe | 25365 | 7179 | 22.06 |
| Aggregation | 30780 | 1764 | 5.42 |
| Dedupe + Aggregation | 24371 | 8173 | 25.11 |
| Max[5] | 28383 | 4161 | 12.79 |
| Max[10] | 30684 | 1860 | 5.71 |
| Max[15] | 31101 | 1443 | 4.43 |
| Max[20] | 31492 | 1052 | 3.23 |
| Max[25] | 31658 | 886 | 2.72 |
| Max[50] | 32485 | 59 | 0.18 |
| pMax[50] | 30963 | 1581 | 4.86 |
| pMax[25] | 30093 | 2451 | 7.53 |
| pMax[20] | 29872 | 2672 | 8.21 |
| pMax[15] | 29449 | 3095 | 9.51 |
| pMax[10] | 28681 | 3863 | 11.87 |
| pMax[5] | 26738 | 5806 | 17.84 |
| dMax[5] (No exclusion) | 26745 | 5799 | 17.82 |
| dMax[5] (US exclusion) | 28362 | 4182 | 12.85 |
| Max[5] + pMax[50] + dMax[5+US] | 27291 | 5253 | 16.14 |
| Dedupe + Aggregation + Max[5] + pMax[50] + dMax[5+US] | 22786 | 9758 | 29.98 |
Installation
Navigate to System > Package Manager > Available Packages.
Scroll down click ‘ Install’ next to pfBlockerNG-devel. The ‘devel’ version is more actively developed and has several significant features implemented beyond the regular version, some of which this guide will take advantage of. The ‘devel’ version has historically been well tested prior to distribution. As always, please test prior to putting into your production use.
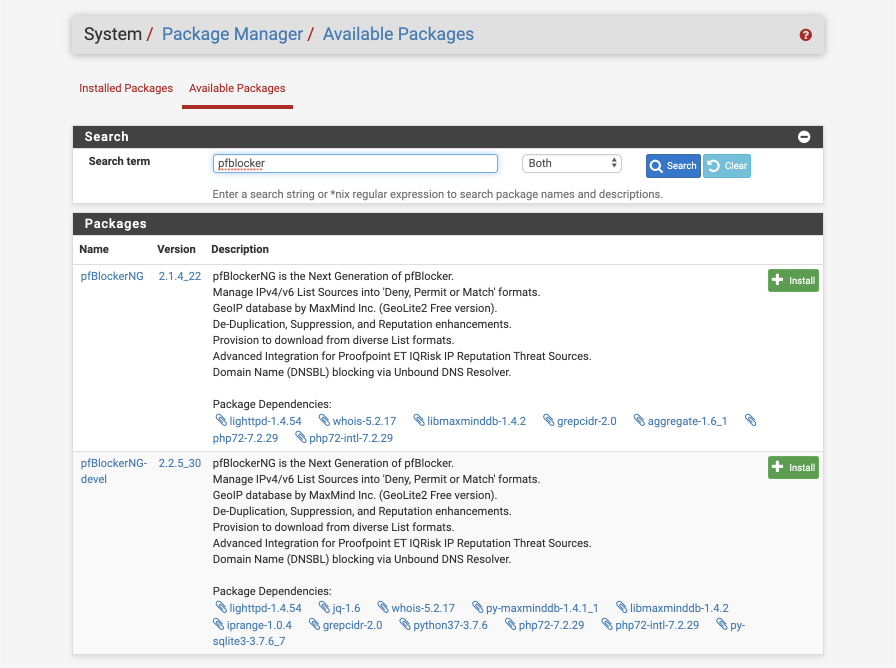
Click Confirm. The installation progress will be displayed in the Package Installation box, verify there are no issues reported.
>>> Installing pfSense-pkg-pfBlockerNG-devel...
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
The following 10 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
pfSense-pkg-pfBlockerNG-devel: 2.2.5_30 [pfSense]
lighttpd: 1.4.54 [pfSense]
lua52: 5.2.4 [pfSense]
jq: 1.6 [pfSense]
whois: 5.2.17 [pfSense]
py37-maxminddb: 1.4.1_1 [pfSense]
libmaxminddb: 1.4.2 [pfSense]
iprange: 1.0.4 [pfSense]
grepcidr: 2.0 [pfSense]
py37-sqlite3: 3.7.6_7 [pfSense]
Number of packages to be installed: 10
The process will require 9 MiB more space.
2 MiB to be downloaded.
[1/10] Fetching pfSense-pkg-pfBlockerNG-devel-2.2.5_30.txz: .......... done
[2/10] Fetching lighttpd-1.4.54.txz: .......... done
[3/10] Fetching lua52-5.2.4.txz: .......... done
[4/10] Fetching jq-1.6.txz: .......... done
[5/10] Fetching whois-5.2.17.txz: ........ done
[6/10] Fetching py37-maxminddb-1.4.1_1.txz: .... done
[7/10] Fetching libmaxminddb-1.4.2.txz: ..... done
[8/10] Fetching iprange-1.0.4.txz: ... done
[9/10] Fetching grepcidr-2.0.txz: ... done
[10/10] Fetching py37-sqlite3-3.7.6_7.txz: .... done
Checking integrity... done (0 conflicting)
[1/10] Installing lua52-5.2.4...
[1/10] Extracting lua52-5.2.4: ......... done
[2/10] Installing libmaxminddb-1.4.2...
[2/10] Extracting libmaxminddb-1.4.2: .......... done
[3/10] Installing lighttpd-1.4.54...
===> Creating groups.
Using existing group 'www'.
===> Creating users
Using existing user 'www'.
[3/10] Extracting lighttpd-1.4.54: .......... done
[4/10] Installing jq-1.6...
[4/10] Extracting jq-1.6: .......... done
[5/10] Installing whois-5.2.17...
[5/10] Extracting whois-5.2.17: .......... done
[6/10] Installing py37-maxminddb-1.4.1_1...
[6/10] Extracting py37-maxminddb-1.4.1_1: .......... done
[7/10] Installing iprange-1.0.4...
[7/10] Extracting iprange-1.0.4: ..... done
[8/10] Installing grepcidr-2.0...
[8/10] Extracting grepcidr-2.0: ..... done
[9/10] Installing py37-sqlite3-3.7.6_7...
[9/10] Extracting py37-sqlite3-3.7.6_7: ........ done
[10/10] Installing pfSense-pkg-pfBlockerNG-devel-2.2.5_30...
[10/10] Extracting pfSense-pkg-pfBlockerNG-devel-2.2.5_30: .......... done
Saving updated package information...
done.
Loading package configuration... done.
Configuring package components...
Loading package instructions...
Custom commands...
Executing custom_php_install_command()...
MaxMind GeoIP databases are not pre-installed during installation.
To utilize the MaxMind GeoIP functionalities, you will be required to register for a free MaxMind user account and access key. Review the IP tab: MaxMind Settings for more details.
Adding pfBlockerNG Widget to the Dashboard... done.
Creating Firewall filter service... done.
Renew Firewall filter executables... done.
Starting Firewall filter Service... done.
Creating DNSBL service... done.
Renew DNSBL lighttpd executable... done.
Starting DNSBL Service... done.
Upgrading previous settings:
Adv. Inbound firewall rule settings... no changes required ... done.
OpenVPN/IPSec interface selections... no changes required ... done.
Proofpoint/ET IQRisk settings... no changes required ... done.
General Tab -> IP Tab settings... no changes required ... done.
pfBlockerNGSuppress Alias -> IPv4 Suppression Customlist... no changes required ... done.
Upgrading previous EasyLists to new format... no changes required ... done.
Upgrading... done
Custom commands completed ... done.
Executing custom_php_resync_config_command()...done.
Menu items... done.
Services... done.
Writing configuration... done.
Success
pfBlockerNG Foundation Configuration
To ensure there are enough entries to store the various tables created by pfBlocker increase the maximum number of table entries pfSense can accommodate. You may need to increase this number higher depending on your final configuration.
Navigate to System > Advanced > Firewall & NAT.
- Firewall Maximum Table Entries = 2000000
Click Save, reboot if prompted.
Navigate to Firewall > pfBlockerNG > General.
Skip the Wizard and you will see the General configuration tab. Apply the following settings.
General Settings
- Enable pfBlockerNG =
- Keep Settings = required to prevent losing settings during upgrades
- CRON Settings =
Every hour,:15,0,0 - Download Failure Threshold = No limit
Log Settings
- Leave as defaults
Click Save
I prefer to use a non-zero offset for the minutes past the hour for the cron job to avoid overloading servers providing blocklists by distributing the access times away from the default configuration.
Malicious IP Address Blocking
Even if the firewall is not configured with open internet facing a ports, one possible attack vector is from local users inadvertently initiating connections to malicious servers. To reduce the chance of this, I recommend blocking access to known sources of Ransomware, malware, botnets and Command & Control (C&C) servers. pfBlocker provides regularly updated blocklists through the bundled PRI1 feed. In this section I’ll cover how to enable the PRI1 group and create the firewall rule to prevent outbound traffic accessing any addresses contained within that group.
IP Blocking Configuration
Navigate to Firewall > pfBlockerNG > IP
IP Settings
- De-duplication =
- CIDR Aggregation =
- Suppression =
- Force Global IP logging =
- Placeholder IP address = 127.1.7.7
- ASN reporting = Enabled (ASN entries cached for 1 hour)
MaxMind GeoIP configuration
To make use of GeoIP functionality you must first register for a free MaxMind user account. Navigate to MaxMind and create an account using the 3.1.1 or newer registration option.
- MaxMind license Key = enter your personal key here
- Maxmind Localized Language = English
- Maxmind CSV updates =
IPv4 Suppression
- Suppression List = empty
IP Interface/Rules Configuration
Although it is possible for pfBlockerNG to automatically create firewall rules, we will later create specific rules into our interfaces.
- Inbound Firewall Rules = NONE
- Inbound Firewall Rules Action = Default
- Outbound Firewall Rules = NONE
- Outbound Firewall Rules Action = Default
- Floating Rules =
- Firewall ‘Auto’ Rule Order = Default
- Firewall ‘Auto’ Rule Suffix = Default
- Kill States =
Click Save
Configure IP Reputation
Navigate to Firewall > pfBlockerNG > IP and select Reputation.
Individual List Reputation
- Max =
- Max Setting = 5
Collective List Reputation
- pMax =
- pMax Setting = 50
- dMax =
- dMax Setting = 5
Country Code Settings
- ccWhite Action: Ignore
- ccBlack Action: Block
- IPv4 Country Exclusion: United States (or select countries you are interested in excluding
Click Save
Enable PRI1 Group
pfBlockerNG offers a collection of predefined blocklists broken down into the following categories.
| Category | Alias/Group | Description |
|---|---|---|
| IPv4 | PRI1 > PRI6 | Known Ransomware, malware, botnets, Command & Control (C&C) servers, bots, web scripts, phishing & compromised servers, malicious IP’s found attacking SSH, SMTP, IMAP, TELNET, FTP end points and other known originators of malicious behaviour. |
| IPv4 | Known sources of spam; useful for protecting mail servers | |
| IPv4 | Tor | Known Tor exit points; not inherently dangerous but you may want to isolate users anonymising their traffic. |
| IPv4 | Internic | Contains root name servers needed to initialize the cache of Internet domain name servers |
The PRI1 through PRI6 lists are high quality, frequently updated, and contain minimal false positives. The same process we use here on PRI1 can be applied to enable other groups too but be mindful that there is a memory and processing impact with each list enabled and it is possible to overload your hardware.
Navigate to Firewall > pfBlockerNG > Feeds.
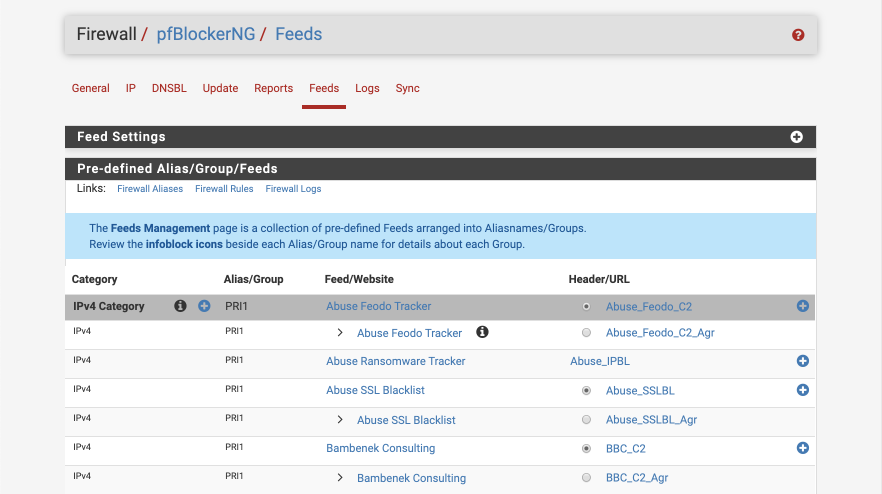
To add the complete PRI1 group, click the under alias/group heading next to PRI1. The at the right of the screen enables you to add individual lists.
- Click
Enable Allto switch all the rule states to ON. - Name = PRI1
- Action = Alias Deny
- Update Frequency = Every hour
- Day of Week = Monday (this is actually ignored as we are updating every four hours)
- Auto-Sort Header field = Enable auto-sort
- Enable logging = Enabled
- States Removal = Enabled
Note: Pulsedive requires a free API key which can be obtained by visiting Pulsedive.
Click Save IPv4 Settings
Invoke first run
Navigate to Firewall > pfBlockerNG > Update
Setting the following options:
- Force Option = Update
Click ‘ Run’
This will start producing a log file in the window below as the update proceeds.
UPDATE PROCESS START [ 04/19/20 05:21:13 ]
===[ DNSBL Process ]================================================
Clearing all DNSBL Feeds
** DNSBL Disabled **
===[ GeoIP Process ]============================================
MaxMind Database downloading and processing ( approx 4MB ) ... Please wait ...
Download Process Starting [ 04/19/20 05:21:13 ]
/usr/local/share/GeoIP/GeoLite2-Country.tar.gz 200 OK
/usr/local/share/GeoIP/GeoLite2-Country-CSV.zip 200 OK
Download Process Ended [ 04/19/20 05:21:21 ]
Country code update Start
Processing ISO IPv4 Continent/Country Data
Processing ISO IPv6 Continent/Country Data [ 04/19/20 05:21:34 ]
Creating pfBlockerNG Continent PHP files
IPv4 Africa [ 04/19/20 05:21:37 ]
IPv6 Africa
IPv4 Antarctica
IPv6 Antarctica
IPv4 Asia
IPv6 Asia [ 04/19/20 05:21:39 ]
IPv4 Europe
IPv6 Europe [ 04/19/20 05:21:43 ]
IPv4 North America [ 04/19/20 05:21:44 ]
IPv6 North America [ 04/19/20 05:21:46 ]
IPv4 Oceania [ 04/19/20 05:21:47 ]
IPv6 Oceania
IPv4 South America
IPv6 South America [ 04/19/20 05:21:48 ]
IPv4 Proxy and Satellite
IPv6 Proxy and Satellite
IPv4 Top Spammers
IPv6 Top Spammers
pfBlockerNG Reputation Tab
Country Code Update Ended
===[ IPv4 Process ]=================================================
[ Abuse_Feodo_C2_v4 ] Downloading update [ 04/19/20 05:21:48 ] .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
1238 1231
------------------
------------------------------
Original Master Final
------------------------------
1238 1231 1231 [ Pass ]
-----------------------------------------------------------------
[ Abuse_IPBL_v4 ] Downloading update [ 04/19/20 05:21:49 ] .. 200 OK. completed ..
Empty file, Adding '127.1.7.7' to avoid download failure.
------------------------------
Original Master Final
------------------------------
0 1 1 [ Pass ]
-----------------------------------------------------------------
[ Abuse_SSLBL_v4 ] Downloading update .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
144 132
------------------
------------------------------
Original Master Final
------------------------------
144 132 132 [ Pass ]
-----------------------------------------------------------------
[ BBC_C2_v4 ] Downloading update [ 04/19/20 05:21:50 ] .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
203 118
------------------
------------------------------
Original Master Final
------------------------------
203 118 118 [ Pass ]
-----------------------------------------------------------------
[ CINS_army_v4 ] Downloading update .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
15000 14215
------------------
------------------------------
Original Master Final
------------------------------
15000 14215 14215 [ Pass ]
-----------------------------------------------------------------
[ ET_Block_v4 ] Downloading update [ 04/19/20 05:21:51 ] .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
2114 2087
------------------
------------------------------
Original Master Final
------------------------------
2114 890 890 [ Pass ]
-----------------------------------------------------------------
[ ET_Comp_v4 ] Downloading update [ 04/19/20 05:21:52 ] .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
848 838
------------------
------------------------------
Original Master Final
------------------------------
848 798 798 [ Pass ]
-----------------------------------------------------------------
[ ISC_1000_30_v4 ] Downloading update [ 04/19/20 05:21:53 ] .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
1000 982
------------------
------------------------------
Original Master Final
------------------------------
8004 774 774 [ Pass ]
-----------------------------------------------------------------
[ ISC_Block_v4 ] Downloading update .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
40 20
------------------
------------------------------
Original Master Final
------------------------------
21 8 8 [ Pass ]
-----------------------------------------------------------------
[ Pulsedive_v4 ] Downloading update [ 04/19/20 05:21:54 ] .. 200 OK. completed ..
------------------------------
Original Master Final
------------------------------
69 68 68 [ Pass ]
-----------------------------------------------------------------
[ Spamhaus_Drop_v4 ] Downloading update [ 04/19/20 05:22:00 ] .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
804 787
------------------
------------------------------
Original Master Final
------------------------------
808 1 1 [ Pass ]
-----------------------------------------------------------------
[ Spamhaus_eDrop_v4 ] Downloading update [ 04/19/20 05:22:02 ] .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
92 75
------------------
------------------------------
Original Master Final
------------------------------
96 73 73 [ Pass ]
-----------------------------------------------------------------
[ Talos_BL_v4 ] Downloading update .. 200 OK. completed ..
Aggregation Stats:
------------------
Original Final
------------------
714 704
------------------
------------------------------
Original Master Final
------------------------------
714 689 689 [ Pass ]
-----------------------------------------------------------------
===[ Aliastables / Rules ]==========================================
No changes to Firewall rules, skipping Filter Reload
Updating: pfB_PRI1_v4
1 table created.18998 addresses added.
===[ Kill States ]==================================================
Firewall state(s) validation for [ 25 ] IPv4 address(es)...
Firewall state(s) validation for [ 1 ] IPv6 address(es)...
No matching states found
======================================================================
===[ FINAL Processing ]=====================================
[ Original IP count ] [ 29258 ]
[ Final IP Count ] [ 18998 ]
===[ Deny List IP Counts ]===========================
18998 total
14215 /var/db/pfblockerng/deny/CINS_army_v4.txt
1231 /var/db/pfblockerng/deny/Abuse_Feodo_C2_v4.txt
890 /var/db/pfblockerng/deny/ET_Block_v4.txt
798 /var/db/pfblockerng/deny/ET_Comp_v4.txt
774 /var/db/pfblockerng/deny/ISC_1000_30_v4.txt
689 /var/db/pfblockerng/deny/Talos_BL_v4.txt
132 /var/db/pfblockerng/deny/Abuse_SSLBL_v4.txt
118 /var/db/pfblockerng/deny/BBC_C2_v4.txt
73 /var/db/pfblockerng/deny/Spamhaus_eDrop_v4.txt
68 /var/db/pfblockerng/deny/Pulsedive_v4.txt
8 /var/db/pfblockerng/deny/ISC_Block_v4.txt
1 /var/db/pfblockerng/deny/Spamhaus_Drop_v4.txt
1 /var/db/pfblockerng/deny/Abuse_IPBL_v4.txt
====================[ Empty Lists w/127.1.7.7 ]==================
Abuse_IPBL_v4.txt
====================[ IPv4/6 Last Updated List Summary ]==============
Apr 16 08:46 Spamhaus_eDrop_v4
Apr 17 04:30 ET_Block_v4
Apr 17 04:30 ET_Comp_v4
Apr 17 05:02 Spamhaus_Drop_v4
Apr 18 23:57 ISC_1000_30_v4
Apr 19 01:57 ISC_Block_v4
Apr 19 04:20 CINS_army_v4
Apr 19 05:04 Talos_BL_v4
Apr 19 05:15 Abuse_SSLBL_v4
Apr 19 05:16 BBC_C2_v4
Apr 19 05:20 Abuse_Feodo_C2_v4
Apr 19 05:21 Abuse_IPBL_v4
Apr 19 05:22 Pulsedive_v4
===============================================================
Database Sanity check [ PASSED ]
------------------------
Masterfile/Deny folder uniq check
Deny folder/Masterfile uniq check
Sync check (Pass=No IPs reported)
----------
Alias table IP Counts
-----------------------------
18998 /var/db/aliastables/pfB_PRI1_v4.txt
pfSense Table Stats
-------------------
table-entries hard limit 2000000
Table Usage Count 19010
UPDATE PROCESS ENDED [ 04/19/20 05:22:11 ]
Create firewall block rule
By preventing a user accessing malicious content behind these addresses, we prevent opening a connection through our stateful firewall which could allow malicious content back in. The alias that pfBlocker created for us in the previous step is now available for use in our firewall rules.
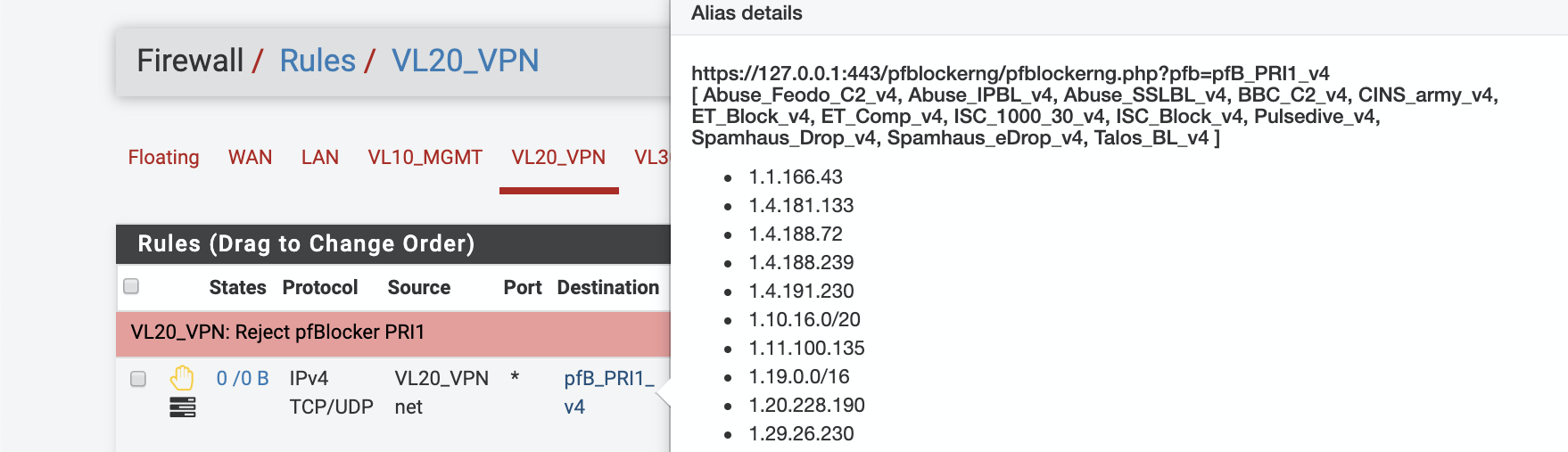
Navigate to Firewall > Rules > VL20_VPN
As rules match in top to bottom priority, we will add the block rule at the top above the permit rules.
Click Add
- Action: Reject
- Disabled:
- Interface: VL20_VPN net
- Address Family: IPv4
- Protocol: TCP/UDP
- Source: VL20_VPN net
- Destination: Single Host or Alias
- Destination Address: pfB_PRI1_v4
- Destination Port range: Any
- Log:
- Description: VL20_VPN: VL20_VPN: Reject PRI1
Click [Save] and Apply.
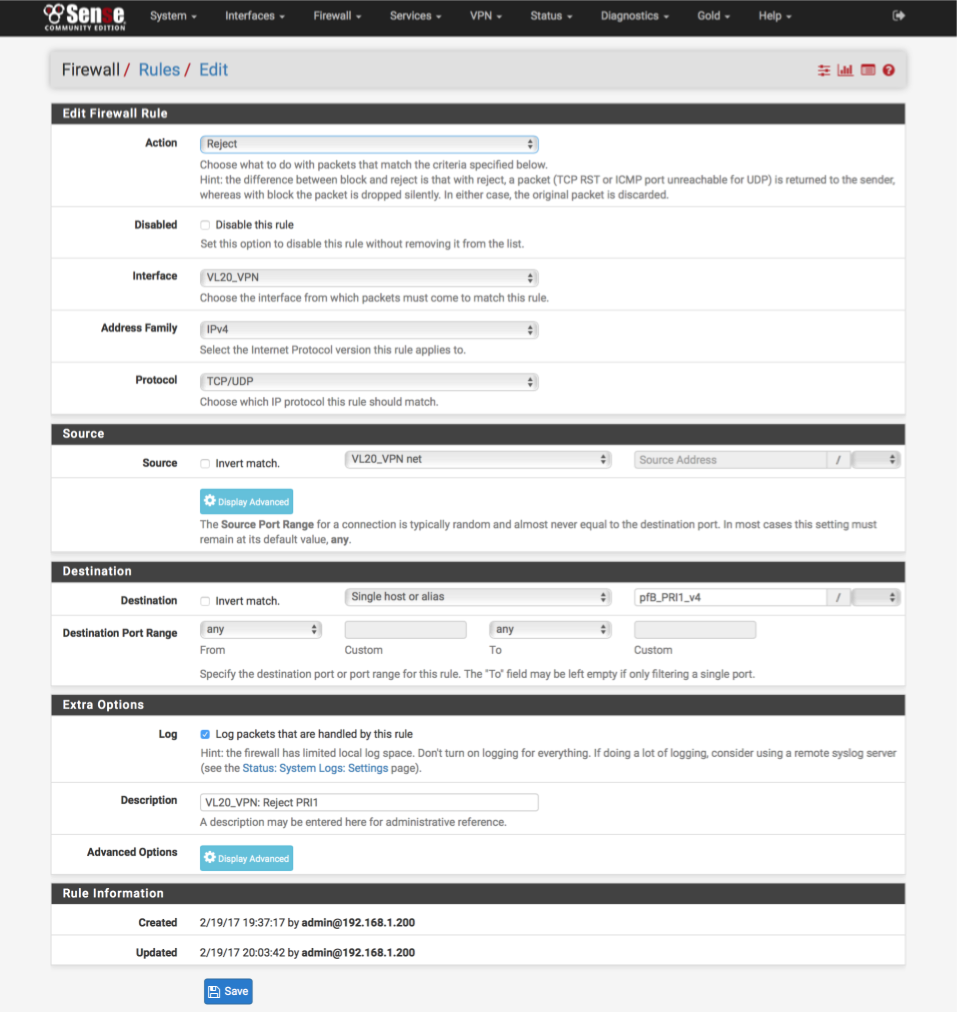
The interface should look like this when complete, note the new reject rule highlighted at the top of the list.
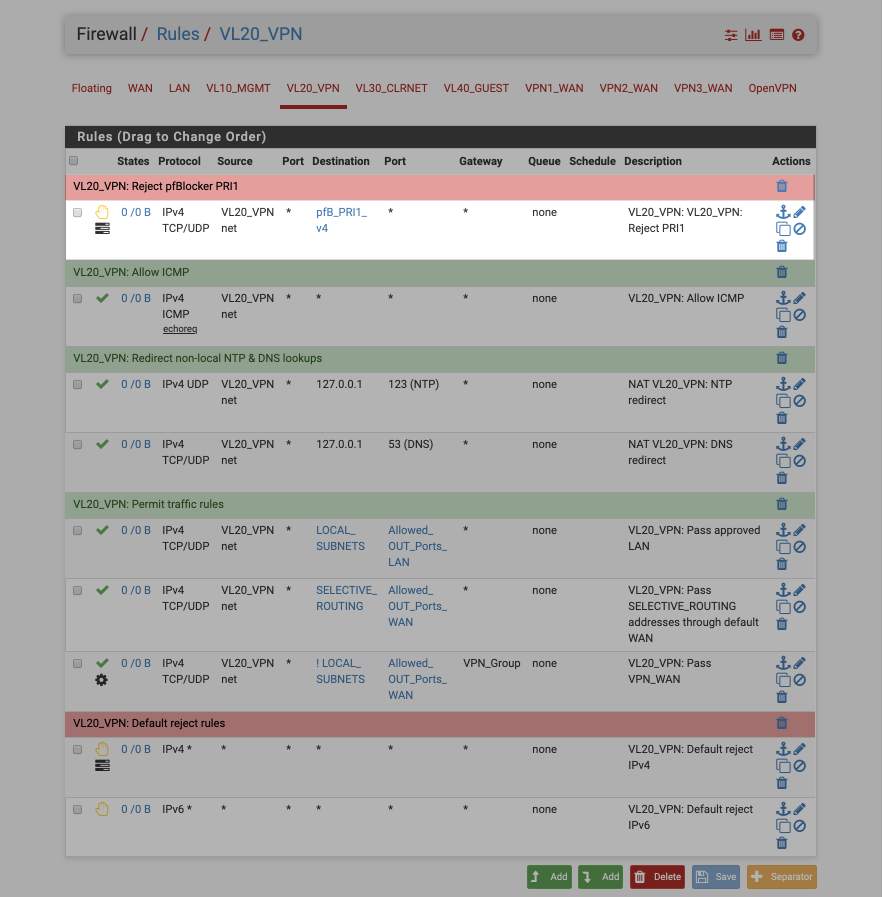
At this point trying to access any of the addresses contained in the PRI1 blocklist from this subnet should result in access being denied. Assuming logging is enabled the Alerts tab will display the attempted access.
Verify PRI1 blocking
To verify our blocking rule is working, hover over the pfB_PRI1_v4 alias name in the firewall rule, this will display a pop-up detailing the aliases contents. Open a browser and try and access one of the IP address, for example http://1.1.166.43.
Your browser should display an error page as it has been unable to contact the server.
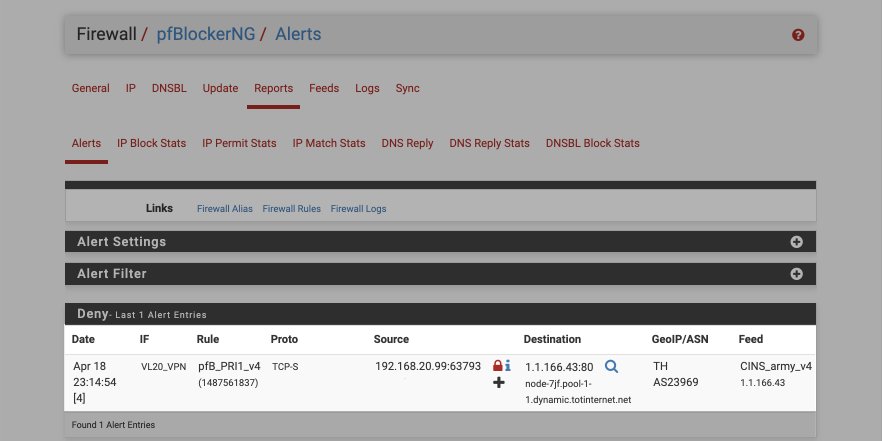
Navigate to the Firewall > pfBlockerNG > Reports and you should see the blocked access displayed. The log entry details the time, source, destination and originating feed. In the case of false positives, you can click on the symbol to whitelist access.
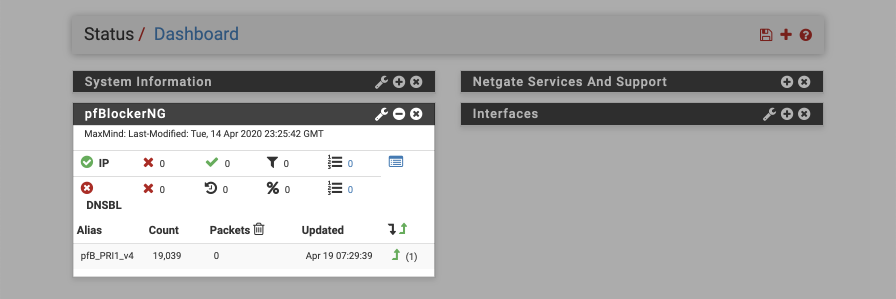
Its also worth enabling the dashboard widget to display performance data on how many matches are being tracked against your blocklists.
Policy based routing with a custom IPv4 list
I use pfBlockerNG to maintain a number of custom lists that are used in various firewall rules to enable policy based routing rules, i.e directing traffic out of specific WAN/OpenVPN interfaces. This mechanism is useful for for sites that don’t respond well to access from VPNs such as financial institutions, media service providers etc.
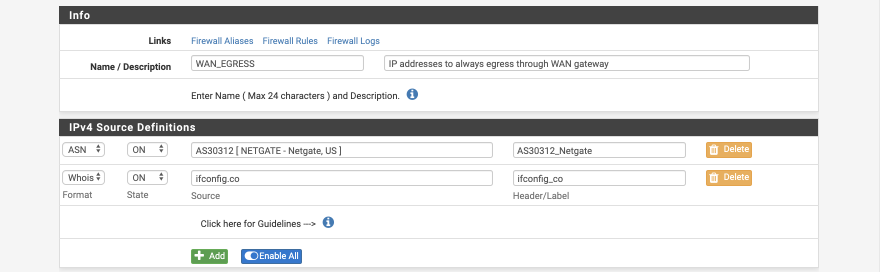
Create WAN_EGRESS alias
In this example we’ll create a IPv4 alias called WAN_EGRESS which includes both a domain name (ifconfig.co) and an AS number (representing Netgate’s IP range). You will use the ifconfig.co domain to verify functionality once complete. This specific alias provides little value and is purely intended as a foundation for you to build your own specific needs upon.
Navigate to Firewall > pfBlockerNG > IP > IPv4
Click ‘ Add’
- Name = WAN_EGRESS
- Description = IP addresses to always egress through WAN gateway
IPv4 Source Definitions
- Format = ASN
- State = On
- Source = AS30312 as you type there will be a prompt to select [ NETGATE - Netgate, US ]
- Header = AS30312_Netgate
Click ‘ Add’ to add another row
- Format = WhoIs
- State = On
- Source = ifconfig.co
- Header = ifconfig_co
Settings
- List Action = Alias Native
- Update Frequency = Once a Day
- Weekly (Day of Week) = Monday (leave as default, it will be ignored due to update frequency)
- Enable Logging = Enabled
- States Removal = Enabled
- Advanced Inbound Firewall Rule Settings = default
- Advanced Outbound Firewall Rule Settings = default
- Advanced Tuneables = default
- IPv4 Custom List = default
Click ‘ Save IPv4 Settings’
Invoke an update of IP lists by navigating to Firewall > pfBlockerNG > Update and set the following options:
- Force Option = Reload
- Reload Option = IP
Click ‘ Run’
In the log display you will see a new line corresponding to our WAN_EGRESS alias called pfB_WAN_EGRESS_v4 reporting the number of IP address contained within that alias.
Alias table IP Counts
-----------------------------
19472 total
19469 /var/db/aliastables/pfB_PRI1_v4.txt
3 /var/db/aliastables/pfB_WAN_EGRESS_v4.txt
To review the contents of this alias list, Navigate to Firewall > pfBlockerNG > Logs and set the following options
- Log/File Type = Alias Files
- Log/File selectin = pfB_WAN_EGRESS_v4.txt
In the log windows you will see the lists data.
208.123.73.0/24
104.28.18.94
104.28.19.94
Configure firewall rule
THis guide will adapt a rule on the VL20_VPN subnet we created in the pfSense baseline guide to direct traffic matching the WAN_EGRESS alias out of the default WAN gateway. This can be used as a illustrative foundation to create rules on other interfaces if required.
Navigate to Firewall > Rules > VL20_VPN
Click the pencil next to the rule containing the SELECTIVE_ROUTING alias and reconfigure this rule as follows.
- Action: Pass
- Disabled = [ ]
- Interface: VL20_VPN
- Address Family: IPv4
- Protocol: TCP/UDP
- Source: VL20_VPN net
- Destination: Single Host or alias
- Address: pfB_WAN_EGRESS_v4
- Destination Port Range:
- From: Other
- Custom: Allowed_OUT_ports_WAN
- To: Other
- Custom: Allowed_OUT_ports_WAN
- Log: [ ]
- Description: VL20_VPN: Pass WAN_EGRESS sites through WAN
- Click [Save]
Make sure the rule ordering is correct and the revised rule is above the rule which allows traffic to exit the VPN interface/group. The interface should look like this when complete, note the new policy routing rule highlighted.
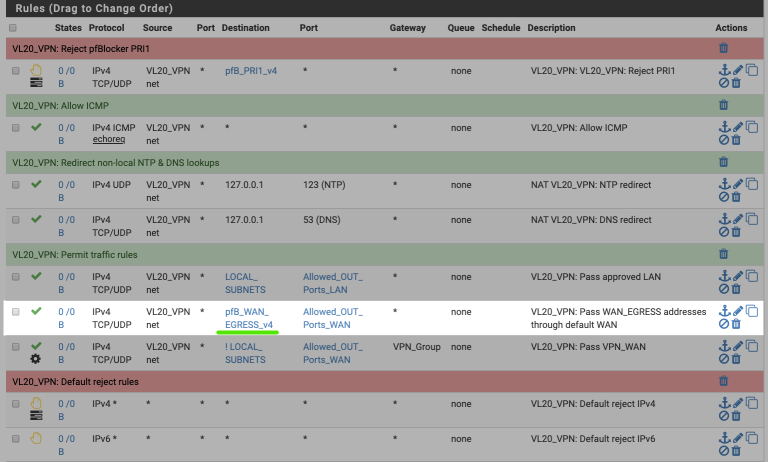
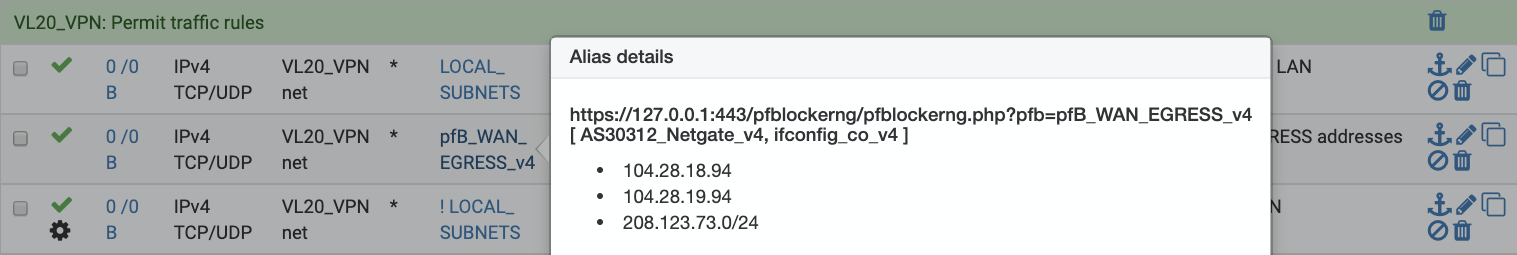
You can hover over the pfB_WAN_EGRESS_v4 alias to see the IP addresses included.
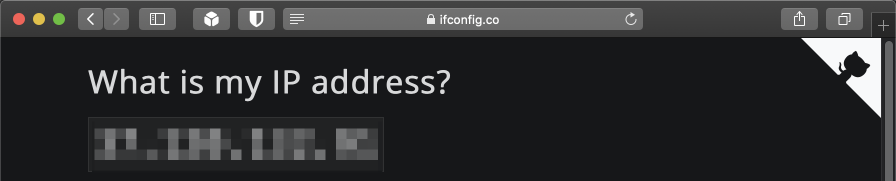
Test policy based routing rule
Connect to your VL20_VPN subnet, open your browser, navigate to https://ifconfig.co. If your rule is working correctly you will see your ISP WAN IP address and not an AirVPN address.
Restrict WAN port access by GeoIP whitelist
If you do not have any ports exposed to the internet, this section will be unnecessary to implement. By default, all inbound ports are default blocked by pfSense. If you do expose an internal proxy, or service, this will be helpful limiting access to that service reducing the chance of unauthorized access. Please consider the implications of opening ports to the internet and only do so when you are confident in your ability to safely protect your network.
I use an alias that includes some geo-located based IP ranges to reduce exposure of self-hosted services to North American IP addresses which is where I typically access them from. If I’m travelling outside North America, I whitelist additional ranges in advance. I also add some other common sources of access to this alias, for example, places of employment,friends and family, and/or mobile carriers.
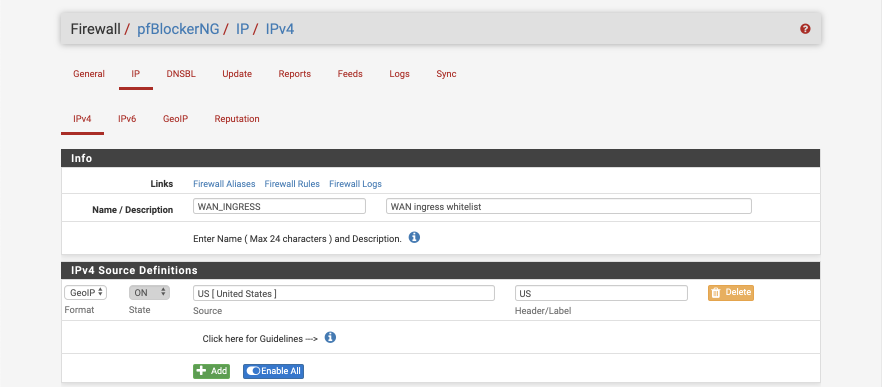
Create WAN_INGRESS alias
Navigate to Firewall > pfBlockerNG > IP > GeoIP
Verify all sources are marked as Action = Disabled.
- Navigate to Firewall > pfBlockerNG > IP > IPv4
Click ‘ Add’
- Name = WAN_INGRESS
- Description = WAN ingress whitelist
IPv4 Source Definitions
- Format: GeoIP
- State: On
- Source: US (as you type you will be prompted with a list of country codes, select your preferred option
- Header/label: US
Settings
- List Action = Alias Native
- Update Frequenct = Once a day
- Weekly (Day of Week) = Monday (leave as default, it will be ignored)
- Auto-Sort Header field = Enable suto-sort
- Enable Logging = Enabled
- States Removal = Enabled
- Advanced Inbound Firewall Rule Settings = default
- Advanced Outbound Firewall Rule Settings = default
- Advanced Tuneables = default
- IPv4 Custom List = default
Click ‘ Save IPv4 Settings ‘
Update the alias by invoking a manual update of IP lists.
Navigate to Firewall > pfBlockerNG > Update, set the following options:
- Force Option = Reload
- Reload Option = IP
Click ‘ Run’
In the log display you you will see a new row in the alias table counts corresponding to our WAN_INGRESS list.
Alias table IP Counts
-----------------------------
79757 total
60312 /var/db/aliastables/pfB_WAN_INGRESS_v4.txt
19442 /var/db/aliastables/pfB_PRI1_v4.txt
3 /var/db/aliastables/pfB_WAN_EGRESS_v4.txt
This alias can now used in our firewall rules.
Apply GeoIP alias to inbound port
We will create a rule on the WAN subnet to permit traffic matching the WAN_INGRESS alias in to our network via port 443.
Navigate to Firewall > Rules > WAN
Select ‘ Add’
- Action: Pass
- Disabled =
- Interface: WAN
- Address family: IPv4
- Protocol: TCP/UDP
- Source:
- Invert Match =
- Single Host or alias
- Address: pfb_WAN_INGRESS_v4 - Destination:
- Invert match =
- Address: WAN address - Destination Port Range:
- From: HTTPS (443)
- To: HTTPS (443) - Log:
- Description: WAN: Allow WAN whitelist ingress
- Save & Apply
Your WAN interface should look this this after clicking Save
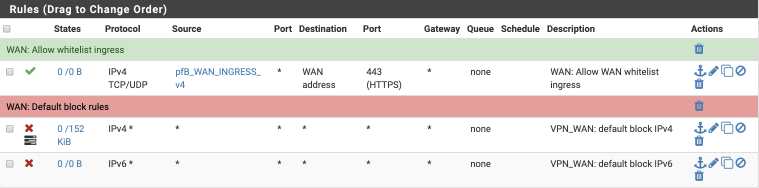
References
MaxMind GeoLite2
grepcidr 2.0
aggregate
Submitting new lists for inclusion in Feeds page
pfBlockerNG is under active development by BBCan177. Please submit new lists for consideration of inclusion in the curated feeds section by emailing BBCan177.
Change Log
20 April 2020
Initial guide published